Researchers have found a new way to steal cars. They use the car’s controller area network(CAN). They also use a simple speaker. They don’t need to smash windows or use FOB code sequences. They can do it in about two minutes. This method has caused bumper and headlight damage.

Car thieves used a new way to steal cars without breaking into them. They tried to steal a Toyota SUV belonging to a cybersecurity expert. The expert discovered that the thieves used a more advanced method than usual. The method was different from both smashing windows and taking control of signals.
Ian Tabor found a vulnerability in Toyota RAV4 cars called CVE-2023-29389. The vulnerability allows car thieves to send fake messages to the car’s system. Thieves can access the car’s CAN bus by removing the bumper and connecting to the headlight connector. Once connected, the thief can send a fake key validation message to start the car and drive away.
Tabor bought a device that looks like a portable speaker. The device has a fake play button wired to a computer chip. When Tabor presses the button, it sends a message to the car’s computer. The message tells the car to unlock the doors. Thieves then remove the device and steal the car. Information on how to make the device is available online.
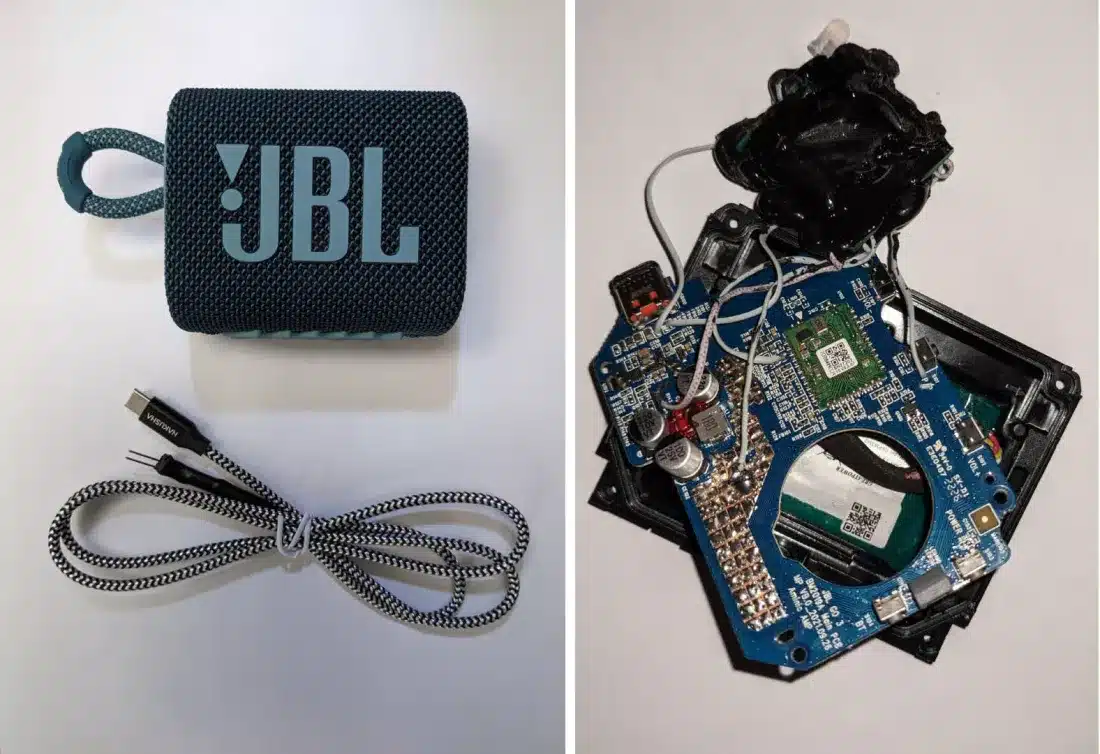
Tabor and Tindell replicated an attack on a Toyota RAV4 car. They think other cars with the same technology could also be vulnerable to this attack. They told Toyota about this problem, hoping they would fix it. However, Toyota has not responded yet.

